Secure Endpoint Manager
The Direct Packet Research Secure Endpoint Management System is a turn-key solution which consists of a Secure Endpoint Manager (SEM), Secure IPC Controller and IPC Routers. These devices when used in conjunction with one another facilitate the simplified integration and expanded reach of a secure global management strategy for IP video and/or audio (VoIP) communication devices and the systems that govern their functionality from one centralized location.
Platform features at a glance
- Single stream TCP port (Default port 443, An alternate port may be selected)
- Security
- AES 256 bit Encryption
- Encapsulated TLS/SSLv3 TCP only traffic
- Block and restrict IP Address
- Integrated Firewall functionality
- Preserve confidentiality
- Signaling and transmission validation
- User and device authentication
- Facilitate IP communications without bridging networks
- Protocols
- HTTP
- HTTPS
- FTP
- TFTP
- SSH
- TELNET
- SNMP
- Application examples
- Interface with third party management systems
- Interface with standalone management station
- Centralized Management and control
- Video Endpoints
- Audio Handsets
- Bridges
- MCU
- Gatekeepers
- PBX
- Firewall traversal
- Single TCP port
- Encapsulated TLS/SSLv3 TCP only traffic
- Traverse one or many firewalls
- NAT traversal
- Liberate public IP addresses
- Network planning
- Eliminate VPN’s
- Simplify Infrastructure and ACL’s
- Web GUI
- Intuitive Interface
- SSL - HTTPS
- SSL certificate management
- IP Access control
- ACL – manage user permissions per device
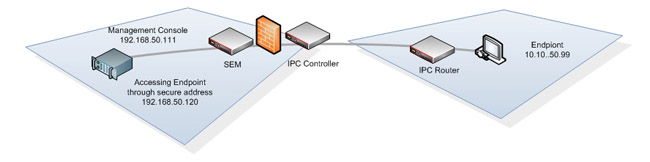
The Secure Endpoint Manager (SEM) is an intelligent internal network device (LAN). Its primary functions are to facilitate the routing, signaling and validation of IP endpoint management and control (HTTP, HTTPS, FTP, TFTP, SSH, TELNET, and SNMP) packets without modifying or impeding the integrity or functionality provided by such packets. The Secure Endpoint Manager (SEM) is positioned in the same Local Area Network (LAN) as the system that governs and manages IP video and/or audio (VoIP) communication devices. The SEM interfaces with a designated Third party management device or a standalone management workstation. When connected to an IPC Controller the SEM provides seamless communication between endpoints and their management host via one single TCP (only)* TLS/SSLv3 AES 256 bit encrypted stream. Once the secure link between the, Secure Endpoint Manager (SEM), Secure IPC Controller, and IPC Routers has been established the solutions then directs and disseminates all management and control packet transmissions to their corresponding destination.
The SEM features an integrated intelligent client/host authentication mechanism and robust protocol validation for providing seamless interoperability with a myriad of devices regardless of their native protocol version or requirements. The benefits to such a technology include:
- Centralized solution management
- Security for the transmission of signaling, management and control data packets
- Expanded reach of network visibility
- Securing the confidentiality of network information
- Non-bridged resolution of isolated and disparate networks
- Firewall and NAT traversal.
*When a Secure Endpoint Manager (SEM) and IPC Routers communicate with a third party management device or a standalone management workstation, the SEM and IPC unit will conform to the native protocols of those devices. When a Secure Endpoint Manager (SEM) and IPC Routers communicate with an IPC Controller and vice versa, all units will conform to TLS/SSL protocol.
The benefits to such a technology include but are not limited to: Providing centralized solution management Base and/or additional security for transport, signaling and media streams Expanded reach of network communication Preservation of confidential network information Non-bridged resolution of isolated and disparate networks Firewall and NAT traversal.
